Blog
A registry cleaner removes redundant entries from the Windows registry. Every computer running windows has its own registry, which is made up of a collection of hierarchical databases. These hold settings for software programs, hardware devices, operating system configurations and more. Whenever a new software program is installed or the user modifies a core system […]
Malicious software, or malware, is a catch-all term for viruses, bugs, trojans, worms and other nasties hackers use to compromise computers. Like a neoplasm, the consequence of an infection depends on the type of malware and how aggressive it is. Malware can wreak destruction on a computer. Without adequate protection, everyone is at risk. If […]
Malware is a collective term for malicious software programs used by hackers and cybercriminals to exploit vulnerabilities in a computer or network. It is dangerous and stealthy, often infecting a computer unbeknownst to the user and sometimes under the nose of an anti-virus program without sufficient detection. Early malware experiments were primitive. They spread locally […]
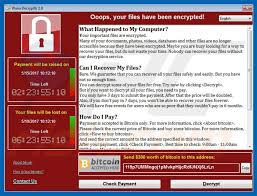
In May 2017, the biggest ransomware attack in history hit the world. The “WannaCry ransomware attack”, as it has since been named, exploited a Microsoft Windows vulnerability in Windows XP and Windows 7 devices. It is unique in that it originated from an exposed, vulnerable internet-facing Server Message Block (SMB) port and not phishing as […]
The internet is interesting, but also dark and full of terrors. Children are particularly vulnerable to the dark side of the web, where criminals lurk to exploit and use them. But it isn’t just the general internet like Google search children should be wary of – cyberbullying on social media is prolific and has been […]
What is Data Privacy Day (DPD) all about? You only need to look at data privacy breaches that have occurred over the last ten years to realise just how vulnerable your personal information is online. In 2013, Yahoo suffered the biggest data privacy breach of all time (and, perhaps, the biggest that will ever occur) […]
Blog Categories
Recent posts
- What is a registry cleaner? 14/03/2019
- Common malware types to look out for 14/03/2019
- What is Malware? 14/03/2019
- NHS caught out by Cyberattack – but could it have all been avoided? 12/05/2017
- What is Safer Internet Day? 07/02/2017
Archives
- March 2019 (3)
- May 2017 (1)
- February 2017 (1)
- January 2016 (1)